Cloud and DevOps merging expertise
and innovation to power your business
Backed by a decade of cloud and DevOps expertise and 24/7 support, we optimize AWS, Azure and GCP environments, turning cloud complexity into scalable growth.
Trusted by 500+ companies to modernize cloud operations and accelerate delivery across the US, Europe and Latin America
Trusted by 500+ companies to modernize cloud operations and accelerate delivery across the US, Europe and Latin America
Proven expertise with real results
With a decade of real execution across modern architectures, 700+ successful projects and 150,000+ engineering hours, we modernize environments, automate workflows and scale platforms securely without expanding your internal engineering teams.
Proven expertise with real results
With a decade of real execution across modern architectures, 700+ successful projects and 150,000+ engineering hours, we modernize environments, automate workflows and scale platforms securely without expanding your internal engineering teams.
Guaranteed 24/7 proactive support
We offer continuous monitoring, incident response and performance optimization around the clock. Our SLAs ensure fast resolution times while proactive actions prevent downtime and vulnerabilities before they disrupt operations.
Guaranteed 24/7 proactive support
We offer continuous monitoring, incident response and performance optimization around the clock. Our SLAs ensure fast resolution times while proactive actions prevent downtime and vulnerabilities before they disrupt operations.
Tailored approaches for every business size
We design and operate infrastructures for companies of all sizes, from early-stage startups to global enterprises. Our delivery model keeps systems stable, scalable and aligned with your growth — regardless of platform maturity.
Tailored approaches for every business size
We design and operate infrastructures for companies of all sizes, from early-stage startups to global enterprises. Our delivery model keeps systems stable, scalable and aligned with your growth — regardless of platform maturity.
Exceptional value at an affordable price
You work with a dedicated team and account manager who ensure continuity and accountability while engineers execute. With enterprise-grade delivery at a competitive cost, you achieve predictable results without increasing hiring or overhead.
Exceptional value at an affordable price
You work with a dedicated team and account manager who ensure continuity and accountability while engineers execute. With enterprise-grade delivery at a competitive cost, you achieve predictable results without increasing hiring or overhead.
Experts across every discipline
Our specialists cover cloud engineering, DevOps, architecture, security, automation and operations. This multidisciplinary capability ensures continuity and precision across every phase, enabling faster delivery cycles and fewer dependency bottlenecks for your team.
Experts across every discipline
Our specialists cover cloud engineering, DevOps, architecture, security, automation and operations. This multidisciplinary capability ensures continuity and precision across every phase, enabling faster delivery cycles and fewer dependency bottlenecks for your team.
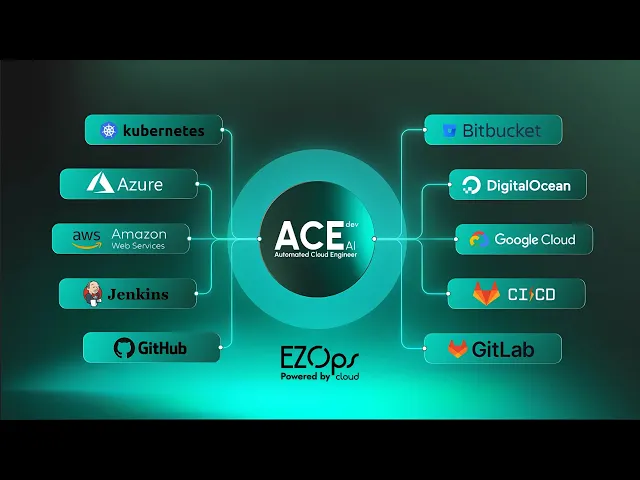
AI-driven cloud optimization
ACE Dev, our agentic AI cloud engineer, automates execution, optimizes environments and accelerates delivery. Trained on real operational intelligence, it reduces repetitive work, increases reliability and evolves infrastructures with fewer delivery bottlenecks.
AI-driven cloud optimization
ACE Dev, our agentic AI cloud engineer, automates execution, optimizes environments and accelerates delivery. Trained on real operational intelligence, it reduces repetitive work, increases reliability and evolves infrastructures with fewer delivery bottlenecks.
CLOUD & DEVOPS CAPABILITIES
Engineering capabilities for cloud-native operations
DevOps & Cloud Engineering
We deliver end-to-end DevOps services that automate workflows, optimize CI/CD pipelines and ensure secure integrations. With real-time monitoring and proactive resolution, we improve reliability, reduce deployment friction and increase operational efficiency — without expanding your internal engineering teams or SRE overhead.
Solutions Architecture
We design cost-efficient, cloud-native architectures aligned with your business goals. Our team builds secure systems, manages integrations and drives ongoing optimization, ensuring platforms remain reliable, adaptable and ready to evolve as demand increases and requirements become more complex.
System Administration
We manage configurations, monitor performance and automate operational routines while mitigating risks and ensuring compliance. With 24/7 support, disaster-recovery planning and proactive oversight, we keep environments secure, efficient and consistently available — enabling uninterrupted delivery and smoother operations.
Real team for real customers
Human expertise powering next-generation operations and intelligent automation — no shortcuts, just real results.
Real team for real customers
Human expertise powering next-generation operations and intelligent automation — no shortcuts, just real results.
Real team for real customers
Human expertise powering next-generation operations and intelligent automation — no shortcuts, just real results.



Original images by the EZOps Cloud team. All rights reserved.
Original images by the EZOps Cloud team.
All rights reserved.
Continuity, accountability and structured delivery are the foundation for predictable results from day one.
Continuity, accountability and structured delivery are the foundation for predictable results from day one.
Continuity, accountability and structured delivery are the foundation for predictable results from day one.
Eliminate reliance on a single engineer
Stop relying on one person. With a full team, you ensure continuity, resilience, and guaranteed delivery, even as priorities and availability change.
Eliminate reliance on a single engineer
Stop relying on one person. With a full team, you ensure continuity, resilience, and guaranteed delivery, even as priorities and availability change.
Eliminate reliance on a single engineer
Stop relying on one person. With a full team, you ensure continuity, resilience, and guaranteed delivery, even as priorities and availability change.
Surpass knowledge limitations
Gain access to senior specialists across cloud architecture, DevOps, security and performance. No one engineer can offer the comprehensive expertise required for enterprise-grade solutions.
Surpass knowledge limitations
Gain access to senior specialists across cloud architecture, DevOps, security and performance. No one engineer can offer the comprehensive expertise required for enterprise-grade solutions.
Surpass knowledge limitations
Gain access to senior specialists across cloud architecture, DevOps, security and performance. No one engineer can offer the comprehensive expertise required for enterprise-grade solutions.
Reduce operational risk
If an expert becomes unavailable, we quickly reassign specialists. No delays, no downtime, and no excuses.
Reduce operational risk
If an expert becomes unavailable, we quickly reassign specialists. No delays, no downtime, and no excuses.
Reduce operational risk
If an expert becomes unavailable, we quickly reassign specialists. No delays, no downtime, and no excuses.
End the lack of commitment
Our engineers are full-time, dedicated, and accountable, ensuring focused delivery aligned with your roadmap, with no distractions or divided attention.
End the lack of commitment
Our engineers are full-time, dedicated, and accountable, ensuring focused delivery aligned with your roadmap, with no distractions or divided attention.
End the lack of commitment
Our engineers are full-time, dedicated, and accountable, ensuring focused delivery aligned with your roadmap, with no distractions or divided attention.
Eliminate communication gaps
Work with experienced, vetted engineers who are fluent in global delivery standards and modern DevOps collaboration practices.
Eliminate communication gaps
Work with experienced, vetted engineers who are fluent in global delivery standards and modern DevOps collaboration practices.
Eliminate communication gaps
Work with experienced, vetted engineers who are fluent in global delivery standards and modern DevOps collaboration practices.
Stop worrying about missed deadlines
Your Project Manager tracks deliverables and ensures timelines are met without hidden trade-offs or extra costs.
Stop worrying about missed deadlines
Your Project Manager tracks deliverables and ensures timelines are met without hidden trade-offs or extra costs.
Stop worrying about missed deadlines
Your Project Manager tracks deliverables and ensures timelines are met without hidden trade-offs or extra costs.
Say goodbye to out-of-control budgets
Budgets are defined upfront, providing full transparency. You’ll know exactly what you're paying for — no surprises, no overruns.
Say goodbye to out-of-control budgets
Budgets are defined upfront, providing full transparency. You’ll know exactly what you're paying for — no surprises, no overruns.
Say goodbye to out-of-control budgets
Budgets are defined upfront, providing full transparency. You’ll know exactly what you're paying for — no surprises, no overruns.
Embrace the future with intelligent automation
ACE Dev automates workflows, accelerates delivery, and brings AI-enhanced processes to your infrastructure, increasing efficiency and reducing manual work.
Embrace the future with intelligent automation
ACE Dev automates workflows, accelerates delivery, and brings AI-enhanced processes to your infrastructure, increasing efficiency and reducing manual work.
Embrace the future with intelligent automation
ACE Dev automates workflows, accelerates delivery, and brings AI-enhanced processes to your infrastructure, increasing efficiency and reducing manual work.
SUCCESS STORIES

LYOS
Your next-generation travel app
"Thiago and his team were super helpful. Great communication, punctual, good availability, and quick turnaround on takeaway tasks. Would highly recommend."
5.0

SWFITGRADE
An app that streamlines grading handwritten tests using your phone's camera
"Great communication, fair price, quick to respond, knowledgeable. Happy with Thiago and the EZOps team. Will surely hire again."
5.0

CAREFUL SECURITY
Building sustainable cybersecurity programs
"Thiago is the master of AWS. He has the solutions to any and all cloud configuration issue. He makes himself available at a short notice and helps with hands-on implementation as well. Very knowledgable and professional!"
5.0

BLOCKVEST MOVEMENT
A tech ecosystem for empowering underserved communities
"Thiago and his team, are experienced and extremely knowledgeable in the Infrastructure and DevOps space. I never needed to worry about the status or get an update as Thiago was providing updates regularly. They did a great job going above and beyond to ensure our Infrastructure was intact and the job was completed satisfactorily!"
5.0

LYOS
Your next-generation travel app
"Thiago and his team were super helpful. Great communication, punctual, good availability, and quick turnaround on takeaway tasks. Would highly recommend."
5.0

SWFITGRADE
An app that streamlines grading handwritten tests using your phone's camera
"Great communication, fair price, quick to respond, knowledgeable. Happy with Thiago and the EZOps team. Will surely hire again."
5.0

CAREFUL SECURITY
Building sustainable cybersecurity programs
"Thiago is the master of AWS. He has the solutions to any and all cloud configuration issue. He makes himself available at a short notice and helps with hands-on implementation as well. Very knowledgable and professional!"
5.0

BLOCKVEST MOVEMENT
A tech ecosystem for empowering underserved communities
"Thiago and his team, are experienced and extremely knowledgeable in the Infrastructure and DevOps space. I never needed to worry about the status or get an update as Thiago was providing updates regularly. They did a great job going above and beyond to ensure our Infrastructure was intact and the job was completed satisfactorily!"
5.0

LYOS
Your next-generation travel app
"Thiago and his team were super helpful. Great communication, punctual, good availability, and quick turnaround on takeaway tasks. Would highly recommend."
5.0

SWFITGRADE
An app that streamlines grading handwritten tests using your phone's camera
"Great communication, fair price, quick to respond, knowledgeable. Happy with Thiago and the EZOps team. Will surely hire again."
5.0

CAREFUL SECURITY
Building sustainable cybersecurity programs
"Thiago is the master of AWS. He has the solutions to any and all cloud configuration issue. He makes himself available at a short notice and helps with hands-on implementation as well. Very knowledgable and professional!"
5.0

BLOCKVEST MOVEMENT
A tech ecosystem for empowering underserved communities
"Thiago and his team, are experienced and extremely knowledgeable in the Infrastructure and DevOps space. I never needed to worry about the status or get an update as Thiago was providing updates regularly. They did a great job going above and beyond to ensure our Infrastructure was intact and the job was completed satisfactorily!"
5.0
CASE STUDIES
Engineering excellence that drives real business impact




The future of cloud operations is intelligent execution
ACE Dev is a 24/7 AI-powered cloud engineer that automates tasks, reduces engineering dependency and delivers results without increasing headcount.

Partner with a trusted cloud team in three simple steps
Partner with a trusted cloud team in three simple steps
Book a discovery call
Share your goals and challenges, and we’ll align on how we can help.
Explore the solution and team structure
We’ll walk you through our tailored solution and introduce the team supporting your cloud needs.
Initiate and monitor progress
We start execution and continuously monitor progress to ensure everything stays on track.



Original images by the EZOps Cloud team. All rights reserved.
Original images by the EZOps Cloud team.
All rights reserved.































































